Table of Contents
Introduction:
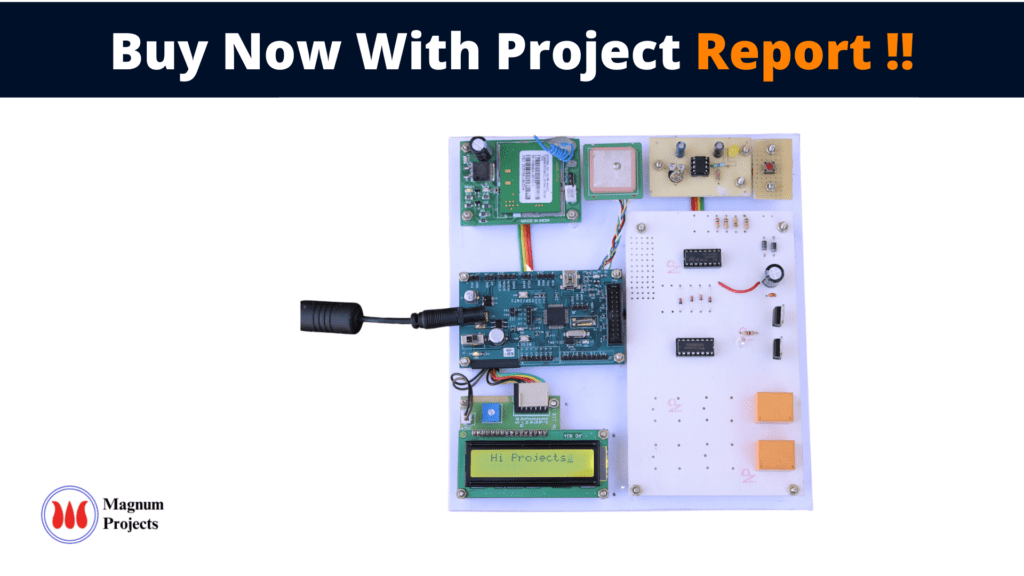
The status of women in India has gone through many great changes over the past few millennia. From equal status with men in ancient times through the low points of the medieval period to the promotion of equal rights by many reformers, the history of women in India has been eventful. In modern India, women have adorned high offices in India including that of the President, Prime Minister, Leader of the Opposition, and Speaker of the Lok Sabah. However, women in India continue to face social challenges and are often victims of abuse and violent crimes, according to a global poll conducted by Thomson Reuters, India is the “fourth most dangerous country” in the world for women, and the worst country for women among the G20 countries. This System focuses on a security system that is designed solely to serve the purpose of providing security to women so that they never feel helpless while facing such social challenges. The system consists of various modules such as a GSM shield (SIM 900A), ARM7 board, GPS, a screaming alarm, a set of pressure sensors for activation, and a power supply unit.
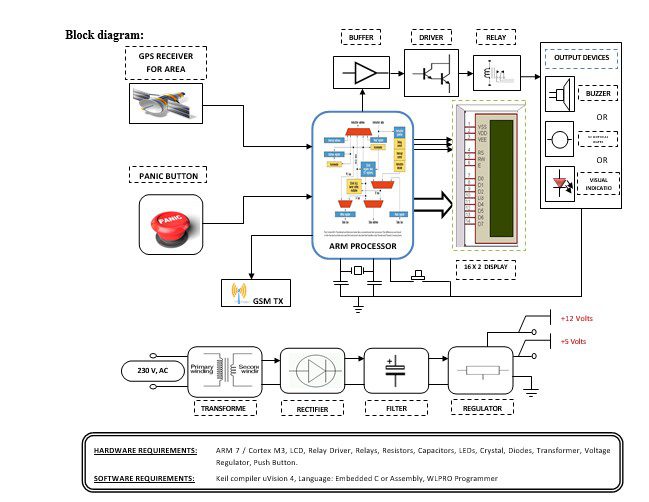
Block diagram explanation :
Power supply unit:
This section needs two voltages viz., +12 V & +5 V, as working voltages. Hence specially designed power supply is constructed to get regulated power supplies.
GPS module:
This is a GPS Receiver (5V Serial) with high gain having 4 Pin 2.54mm pitch strip. The third-generation POT (Patch Antenna on Top) is used by the receiver for the GPS module. It can be interfaced with normal 5V ARM7 with the help of the in-built 3V-5V converter. The interfacing is made easier with the help of a low pin count (4-pin) strip. The 4 Pins are 5V, TX, RX, and GND. This standalone 5V GPS Module does not require external components. It consists of an internal RTC Back up battery and can be directly connected to the USART of the ARM7.
The current date, time, longitude, latitude, altitude, speed, and travel direction / heading among other data, are provided by the module and can be used in many applications including navigation, fleet management, tracking systems, mapping, and robotics. The module can support up to 51 channels. The GPS solution enables small form factor devices which deliver major advancements in GPS performance, accuracy, integration, computing power, and flexibility. They are used to simplify the embedded system integration process.
GSM:
GSM Shield (SIM 900a): The SIM900 which is a complete Quad-band GSM/GPRS solution comes in a SMT module that can be embedded in customer applications. Featuring an industry-standard interface, the SIM900 delivers GSM/GPRS 850/900/1800/1900MHz performance for Data, voice, SMS, and Fax in a small form factor and with low power consumption. SIM900 can fit almost all the space requirements in the M2M application with dimensions of 24mm x 24mm x 3 mm. SIM900 is designed with a very powerful single-chip processor integrating AMR926EJ-S core. Quad-band GSM/GPRS module with a size of 24mmx24mmx3mm, SMT type suit for customer application, An embedded Powerful TCP/IP protocol stack Based upon the mature and field-proven platform, backed up by our support service, from definition to design and production.
NOTE: Modem may change.
ARM processor:
ARM is a computer processor-based RISC architecture. A RISC-based computer design approach means ARM processors require significantly fewer transistors than typical processors in average computers. This approach reduces costs, heat, and power use. The low power consumption of ARM processors has made them very popular:
The ARM architecture (32-bit) is the most widely used in mobile devices, and the most popular 32-bit one in embedded systems.
ARM processor features include:
- Load/store architecture.
- An orthogonal instruction set.
- Mostly single-cycle execution.
- A 16×32-bit register.
- Enhanced power-saving design.
Buffers:
Buffers do not affect the logical state of a digital signal (i.e. a logic 1 input results in a logic 1 output whereas logic 0 input results in a logic 0 output). Buffers are normally used to provide extra current drive at the output but can also be used to regularize the logic present at an interface.
Drivers:
This section is used to drive the relay where the output is the complement of input which is applied to the drive but the current will be amplified.
Relays:
It is an electromagnetic device that is used to drive the load connected across the relay and the o/p of the relay can be connected to the controller or load for further processing.
Indicator:
This stage provides a visual indication of which relay is actuated and deactivated, by glowing respective LED or Buzzer.
Methodology:
In today’s world, many women employees are facing the problem of security which is taking place around the world, especially across India. So our main aim is to avoid the problems of women by developing a system that can be implemented in real-time. And protect them at night duties while returning home from job. The same project can be implemented in several applications in real-time like protecting children from children kidnapers and some are listed below. We are also implementing an application called the report of accidents to vehicles carried by them automatically via the GSM.
Advantages:
- Women can go anywhere with more security.
- Avoids women’s rape.
- Culprits can be easily found and can be punished
- Consumes less power
- Provides very accurate data via GPS.
- Allows the remote location of assets from anywhere there is cellular Service.
- Facilitates simple asset recovery and tracking.
Disadvantages:
- The only thing that is clear about constitutional protections for location-based service information is the lack of clarity.
Applications:
- It can be used to safeguard women in critical conditions.
- It can be used to detect vehicles under theft.
- It can be employed for tracking any movable objects.
- Fleet control.
- Stolen vehicle searching.
- Animal control.
- Race control.
- Espionage/surveillance.