Table of Contents
Introduction:
Current research activities in vehicular on-board IT architectures follow two key trends: unification of network communication and centralization of functionality. Recent on-board IT architectures comprise a very heterogeneous landscape of communication network technologies, e.g., CAN, LIN, Flex Ray, and MOST. Internet Protocol (IP) based communication is currently being researched as a technology for unifying the overall interconnection of ECUs in future on-board communication systems. State-of-the-art vehicular onboard architectures consist of up to 70 Electronic Control Units (ECU), which are interconnected via different bus communication systems. To substantiate economic aspects, such as vehicular weight reduction by saving ECU hardware resources or increasing maintainability, the trend is towards the centralization of functionality. The centralization of single ECU functions on multipurpose ECUs allows for a significant reduction of the overall number of in-vehicle ECUs and hence helps to mitigate the overall complexity. Open standards and interfaces need to be created to create platforms, where software from different suppliers can be steadily integrated. Besides these trends in the design of automotive on-board IT architectures, new external communication interfaces, fixed and wireless are becoming an integral part of on-board architectures. One key factor for this development is the integration of future e-Safety applications based on V2X communications that have been identified as one promising measure for decreasing the number of fatal traffic accidents. In addition, user electronic devices, such as smartphones or music players are increasingly integrated in vehicle infotainment systems. However, adding external interfaces to vehicular on-board architectures poses new security threats to these systems. Specifically safety applications need to be secured against malicious attacks. Key security requirements of safety applications and safety-related information are integrity, authenticity, and trustworthiness. Applying virtualization techniques on multipurpose ECUs support these security requirements, as this technology provides the separation of processes and applications, and hence allows for the execution of applications with different trust levels on the same ECU. As application domains with varying trust levels may communicate within the onboard network, it is reasonable to additionally provide respective security measures to control the information flow amongst such domains. We believe that the combination of virtualization and Trusted Computing technologies (e.g., based on Trusted Platform Modules) provides the measures for meeting our discussed security requirements. An approach to provide a software and hardware security architecture will be the outcome of the EVITA project (E-safety Vehicle Intrusion Protected Applications) of the Seventh European Framework Program, which aims to design, verify, and prototype a security architecture for vehicular on-board networks, where all security-relevant components and sensitive information are protected against tampering and malicious manipulations. Thus, EVITA implements the security technology for vehicular communication endpoints, enabling the security of safety applications, but also most other V2X communication applications (e.g., vehicular comfort, or business applications).
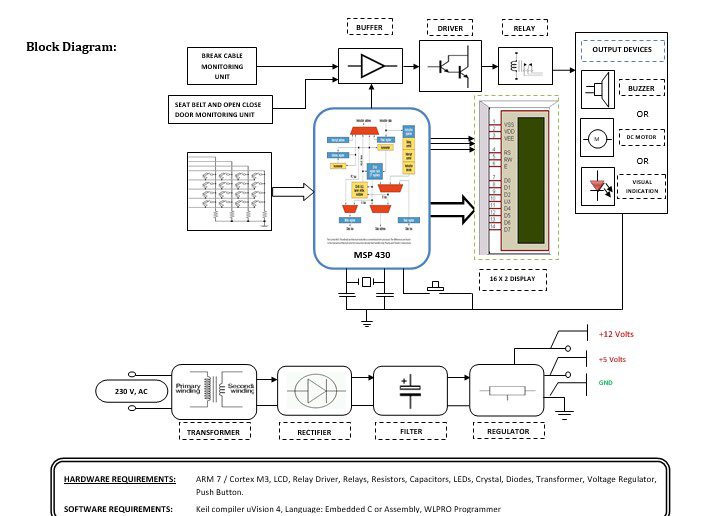
Block diagram explanation:
Power supply unit:
As the whole RF Transmitter Unit goes with the vehicle, its power supply must be kept compact and compatible with all kinds of vehicles and their power generators.
MSP 430 Controllers:
Here the MSP 430 is used to check the password which has been entered from the keyboard. If the password is correct it generates the output accordingly. The output of this section is connected to Buffer & Driver unit for further processing.
Buffer:
Buffers do not affect the logical state of a digital signal (i.e. a logic 1 input results in a logic 1 output whereas logic 0 input results in a logic 0 output). Buffers are normally used to provide extra current drive at the output but can also be used to regularize the logic present at an interface.
Driver:
This section is used to drive the relay where the output is the complement of input which is applied to the drive but the current will be amplified.
Relay:
It is an electromagnetic device that is used to drive the load connected across the relay and the o/p of the relay can be connected to the controller or load for further processing.
Methodology:
A block diagram is shown above the vehicle which monitors the seat belt, opens or closes the door & breaks the cable. Any variation in parameters gives that signal to the MSP 430 controller, and then the MSP 430 controller performs the required function and displays the message. At the same time, MSP430 will generate the output that is fed to buffer IC 4050, buffer stores and given to the driver IC 2003 in driver current will amplify and voltage will invert with the help of Darlington circuit of driver IC to drive the relay. Then the signal is given to the output load for indication purpose
Advantages & Disadvantages:
Advantages:
- As a security device for all vehicles.
- Also for automatic operation of the gates.
- More useful in remote areas.
- This project we can operate Easily
Disadvantages:
- It increases the cost whereas digital systems reduce the cost of the system.
Applications:
1. Automotive Applications.
2.Home and Office Applications.
3.Home and office automation.
4.Smart environment.
5.Environmental Applications.
6.Military Applications.
7.Monitoring friendly forces, equipment, and ammunition.
8.Battlefield surveillance.
9.Reconnaissance of opposing forces and terrain.